The Secure360 Process.
The Secure360
Process.
Camelot Secure offers a revolutionary approach to cybersecurity, combining an elite team of professionals with extensive military and cyber expertise with our unified Secure360 platform. In today’s evolving threat landscape, a comprehensive 360-degree view is essential. By partnering with Camelot Secure, your team gains proactive defense strategies designed to keep you “left of boom”—preventing attacks before they happen.
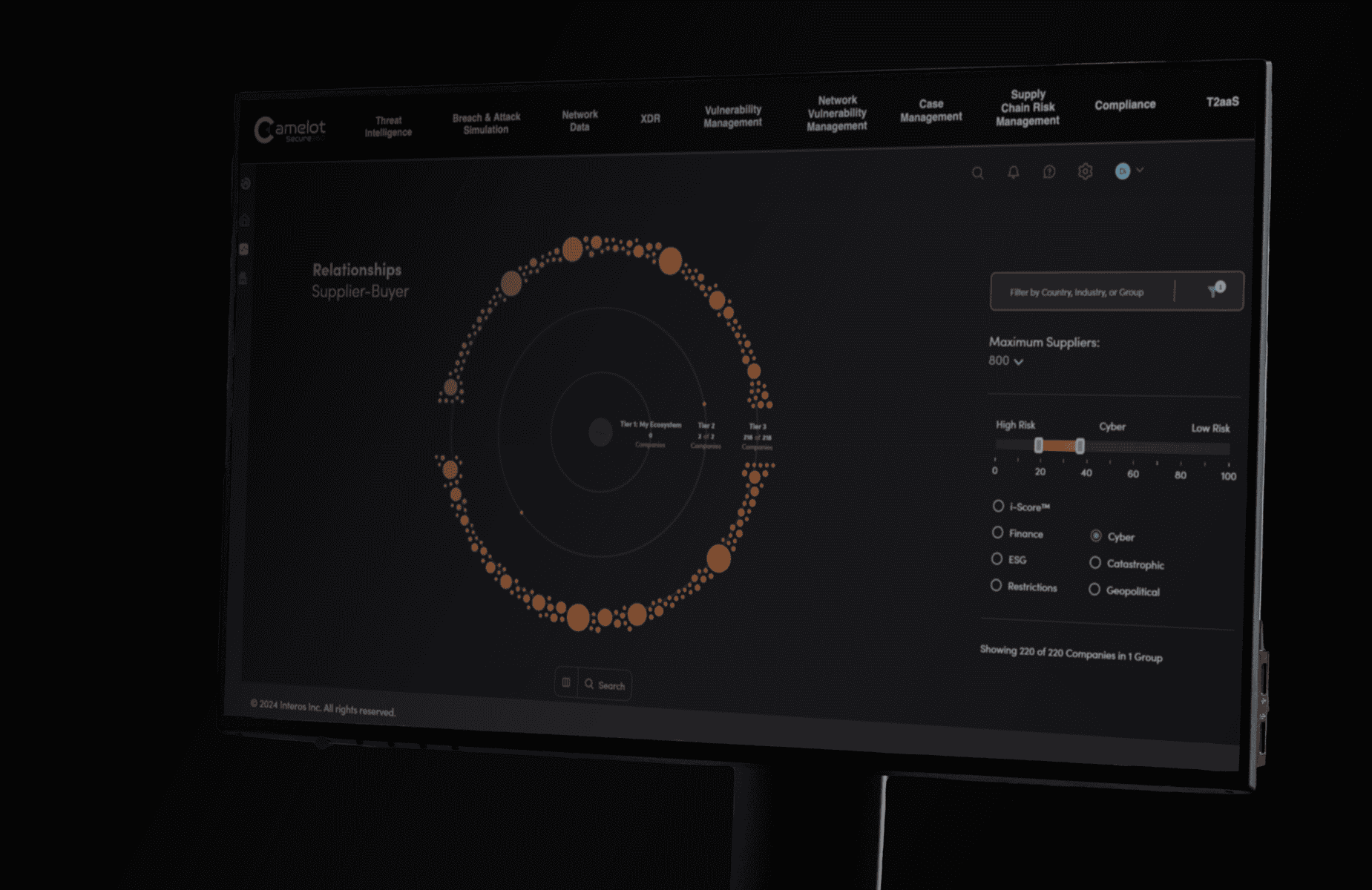
Secure360 Solutions
A select suite of comprehensive services curated to meet all of your cybersecurity needs.
Playbooks
Playbooks
APT: Advanced Persistent Threat Hunting – solutions to help you scale with speed.
APT: Advanced Persistent Threat Hunting – solutions to help you scale with speed.
APT Hunting is proactively seeking out and identifying advanced and persistent cyber threats actively trying to infiltrate an organization’s networks and systems. It is a continuous and iterative process that involves collecting, analyzing, and interpreting data from various sources to detect potential threats and prevent them from causing damage.
Camelot Secure360 Advanced Persistent Threat Hunting can make measurable differences in your Cybersecurity defenses.
Preparation is key.
Preparation is key.
It’s not if but when you are attacked.
You simply can’t afford to be unprepared.
The initial financial loss is often just the beginning as data breaches can harm a business or organization’s reputation and lead to customer loss or a need to increase costs to consumers.
Trust Nothing, Secure Everything:
Zero Trust Security for the Modern Enterprise
Trust Nothing, Secure Everything:
Zero Trust Security for the Modern Enterprise
With decades of experience, we have worked in the most demanding environments across the globe, providing the elite guidance and innovation necessary to protect our customers’ most critical assets.
In today’s interconnected business landscape, traditional security perimeters have dissolved. Camelot’s Secure360 platform employs a comprehensive zero trust architecture. By implementing proactive threat hunting, comprehensive vulnerability assessment, advanced EDR & SOAR, and real-time threat analysis, our solution ensures that only authenticated and authorized entities can access your sensitive resources. This “never trust, always verify” approach provides your organization with an adaptive security framework that evolves with emerging threats while maintaining seamless operations for legitimate users.
Confidently Secure.
Confidently Secure.
“Camelot Secure has emerged as a leading provider of integrated cybersecurity solutions, renowned for its cutting-edge technology and comprehensive approach to security.”
Beth Kramer, CEO, Engenix, Inc.


